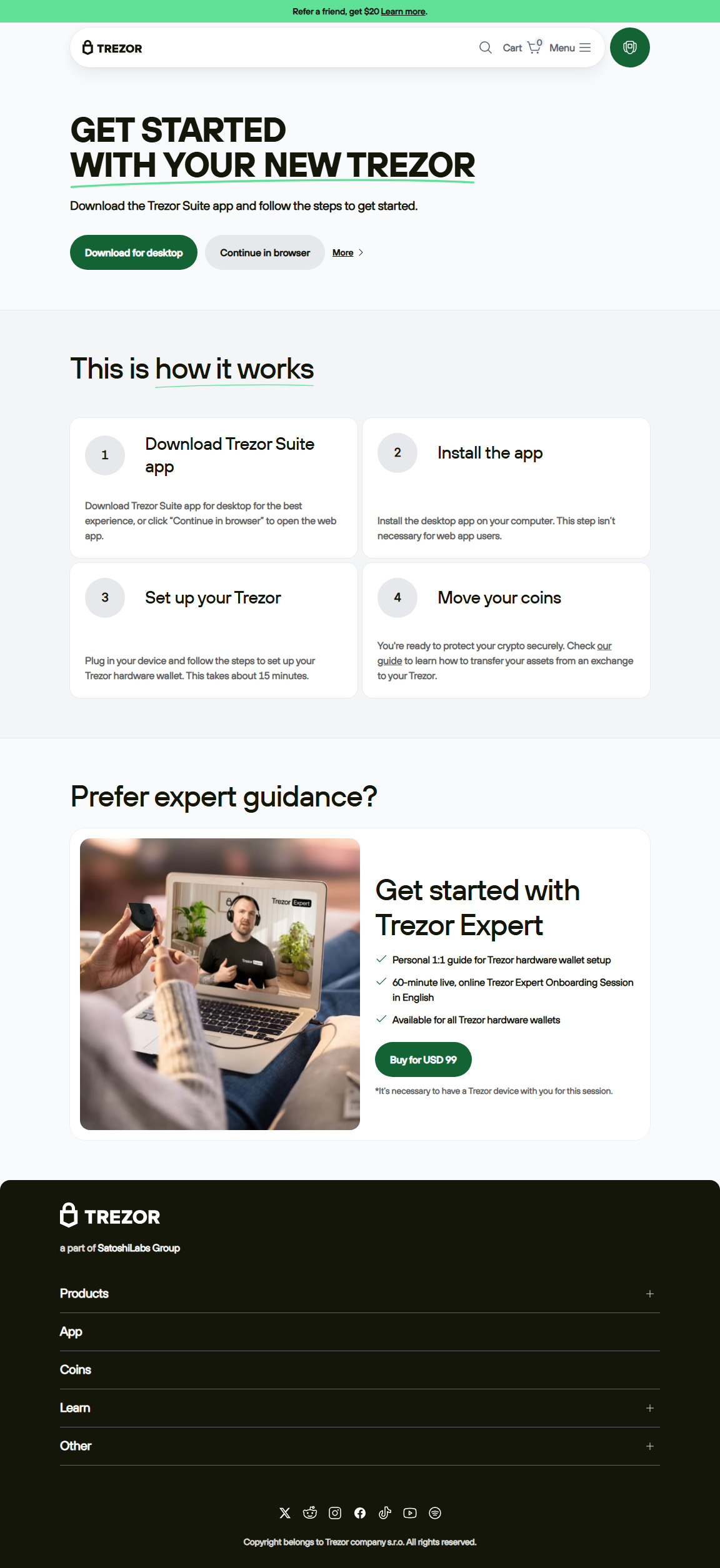
trezor.io/start — Secure Setup, Confident Ownership
A practical, attack-aware walkthrough for initializing your Trezor hardware wallet. Learn the safe path — from verified downloads to recovery seed best practices — framed for beginners and experienced users alike.
What is trezor.io/start?
trezor.io/start is the official onboarding portal provided by Trezor (SatoshiLabs) for initializing and configuring your Trezor hardware wallet. It’s the safe, canonical place to download the Trezor Suite app, verify firmware, and follow step-by-step setup instructions that minimize exposure to phishing or tampered software.
The setup moment is the most sensitive time for any wallet — a single mistake (fake installer, leaked recovery words) can permanently compromise funds. Start at the official page and treat each step as security-critical.
Quick checklist
• Type trezor.io/start manually — don’t click ads or emails.
• Download Trezor Suite from that page.
• Initialize device, write seed on paper/metal, store offline.
• Test with a small transaction.
Step-by-Step: Safe Setup Flow
1 — Verify the page
Open a clean browser window and type trezor.io/start directly. Confirm the domain, browser lock icon, and certificate details if needed. Bookmark it for future use.
2 — Download Trezor Suite
Choose the signed installer for your OS (Windows / macOS / Linux). Trezor Suite is the official desktop application that handles firmware updates, account management, and transaction signing.
3 — Connect your Trezor
Use the provided USB cable. Allow the Suite app to detect and initialize the device. If prompted, install firmware only through the Suite — never accept firmware from untrusted sources.
4 — Create your wallet & seed
Follow on-screen steps to create a new wallet. The device will generate a random recovery seed (12, 18 or 24 words depending on model). Write it down exactly and store it offline — this seed is the only recovery method.
5 — Secure your seed
Do not photograph, store in cloud notes, or type the seed on a computer. Use paper or a metal backup plate for long-term durability. Consider geographic separation and a trusted safe deposit if funds are significant.
6 — Set a PIN and optional passphrase
PIN protects the device if stolen. A passphrase (additional secret) can create hidden wallets — powerful but with added responsibility (passphrase loss = funds loss).
7 — Test with a small transfer
Send a small amount from an exchange or another wallet to confirm receipt and that you can create and broadcast transactions successfully.
Seed security — rules that matter
- Write by hand on a dedicated recovery card or metal backup.
- Store copies in two separate secure locations (not in the same home).
- Never enter seed words into a computer or phone.
- Consider a simple inheritance plan so heirs can recover assets if needed.
Common setup pitfalls
Downloading installers from searches/ads: risky — always use trezor.io/start.
Photographing seeds: vulnerable to cloud leaks or device compromise.
Skipping a test transaction: don't skip — it validates the whole flow.
Trezor model snapshot — choose what fits
Trezor Model T
Color touchscreen, support for wide coin selection, SD card option for higher security workflows.
Trezor One
Proven, budget-friendly, strong security fundamentals — ideal for straightforward cold storage.
Why official purchase matters
Buying from authorized channels reduces the chance of receiving a tampered device.
Practical post-setup measures
- Record firmware version and keep Trezor Suite updated — firmware updates patch security issues and add features.
- Consider using a passphrase for large holdings (understand the responsibility first).
- Periodically inspect the physical device for signs of tampering before use.
- Keep a minimal hot wallet for everyday small transactions — do not mix large sums with daily convenience wallets.
A simple comparison: Hardware vs. Software wallets
Hardware wallet
Keys stay offline; stronger protection against remote attacks; best for long-term storage.
Software wallet
Convenient for frequent trading; higher exposure to malware and phishing.
Short FAQ
Q: Can I setup without trezor.io/start?
A: You can—but doing so increases risk. The official page provides verified installers and guidance which reduce setup vulnerabilities.
A: You can—but doing so increases risk. The official page provides verified installers and guidance which reduce setup vulnerabilities.
Q: What if I lose my device?
A: Restore your wallet with your recovery seed on another Trezor or compatible wallet. If seed is lost, funds are irrecoverable.
A: Restore your wallet with your recovery seed on another Trezor or compatible wallet. If seed is lost, funds are irrecoverable.
Q: Should I use the passphrase feature?
A: It adds strong protection and can create hidden wallets — useful for advanced users. However, losing the passphrase equals losing access, so treat it like a second seed.
A: It adds strong protection and can create hidden wallets — useful for advanced users. However, losing the passphrase equals losing access, so treat it like a second seed.
Start securely at trezor.io/start — one careful setup protects you for years.
If you shop, buy only from official stores or verified resellers. If you set up, follow the official Suite and treat your recovery seed as the most valuable item you own.